Cybersecurity’s Final Frontier
Originally Posted on Medium on Feb 14th, 2019
With the increasing demand for business agility and the maturing of cloud technologies, cyber security must evolve to remain relevant.
Abstraction is the essence of the digital transformation.
Virtualization abstracted physical data centers, cloud abstracted operating systems and application infrastructures, giving developers and the business direct access to resources without the need to manage their infrastructure (e.g. databases, web servers, api gateways etc.).
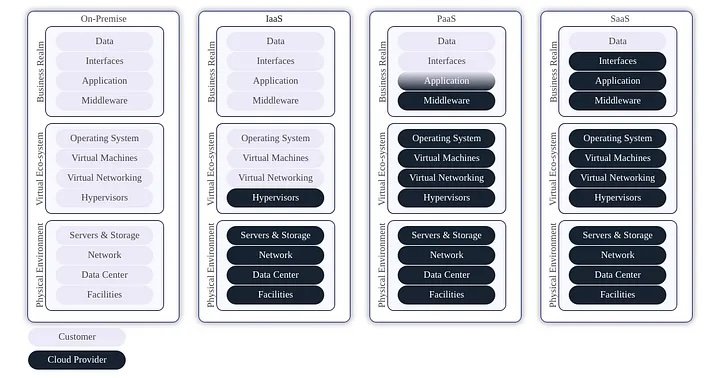
Responsibility Shifts as transformations continue to take place
How about security?
While Security teams are expected to win the continuous cyber war against hackers, they remain stranded with minimal to no tools in the toolbox. The cloud causes traditional control planes to be obsolete, from firewalls and IPS’s to host based security tools, current technologies cannot be implemented in an effective and constructive manner.
Unfortunately, the compensating controls provided by cloud providers doesn’t make the cut, taking security back a decade. Where every basic firewall today has layer 7 understanding, IPS/IDS, User Awareness and other functions — leading cloud vendors only provide basic routing and packet filtering.
Today’s security is left with two applicable control planes: Application & Data
Application security has been an integral part of the cyber security industry for years; with Microsoft’s SDLC and OWASP paving the way, organizations attempted to implement those methodologies into their product lifecycle. But the problem with application security has always been compensating security controls; Amending the behavior of developers and their management has proven to be harder than investing money in firewalls, Anti-X’s and other controls.
Nowadays, we are reaching a where money will not be able to compensate on the lacking in application security, and lacking application security would directly mean inviting a breach. The security domain is in an intersection point; Continuing to attempt and enforce obsolete compensating controls, or taking the security to the next level and protecting the core of the organization, the business.
The Next Security Evolution
The decay of traditional security controls requires the CISO to rethink his strategy, method of operation and establish new partnerships within the organization to drive security upstream and manage security in the “business realm” .
The solution is relatively easy to describe, but hard to implement. embedding security within the development process from the get-go can reduce the likelihood of an application vulnerability, increase the resiliency and overall stability of the application but it requires the engagement of teams outside of the security group, which have different objectives and interests.
Automating Security Delivery
The introduction of CI/CD methodologies, combined with Agile development practices have exponentially increased the organization's ability to deliver very fast solutions to the market, up to a point where versions are released to production every couple of hours. While most parties within the product development lifecycle advanced and adjustments aimed at reducing the time-to-market, the security group remained behind, using manual processes and antique technics.
In the past, while no one liked going through security but there was no other way. The business needed firewall rules to be configured, servers to be installed and those were out of reach without security signoff. The manual processes imposed by security caused severe delays in the product timelines or risk taking by the organization but in the context of waterfall development and yearly release of a product / version that was manageable.
For the security to remain relevant and the collaboration model to work, security must adopt Shift to the left, adopt automation techniques similarly to the ones used by dev and ops teams and enable security throughout the product life cycle.
Security Shift Left
Starting from the get-go, If security take active part in the product life cycle, it can reduce the need for traditional security controls which are less applicable due to the cloud abstractions.
Within each of the phases security can add value, gain insights and embed security controls, creating an actionable application security coverage without concerns of lacking control planes such as the network and infrastructure.
In example, by defining and managing an identity for each application component, the ecosystem can enforce boundary protection that is not based on IP addresses or networking segments. For security, this proves to be the holy grail as the interaction between components is now being driven by business need rather than obscure policies which are never as fine-tuned nor sustainable.
Other examples includes promoted secure libraries for faster coding by the developers, automated code scanning and enablement of open source consumption in a secure manner.
Conversion of Security business logic to security requirements can occur throughout the CI/CD pipeline to validate the deployment is made in a secure manner. The interaction between security and the CI/CD pipeline assist the business in delivering fast, with limited to no security friction and manual approval processes — If it is within the boundaries of the defined policies, it does not require any security approval at all.
The Security Collaboration model
The method of achieving state-of-the-art security starts with the collaboration of the security team with the developers and operations teams. Each of the teams can contribute a portion of the information to create a solid security suit.
Secure Collaboration Model
Correlating inputs provided by the teams generates a blueprint for a secure application and acts as a whitelist of methods, functions and interactions opposed to obscure compensating controls which work in a blacklist model (e.g. web application firewall looking for attack signatures).
The value of the secure collaboration model lays within its ability to decentralize the process of security management and overlaying. With the security teams predefining the security guardrails for a product / project, the developers and Ops teams have the freedom of operating within those guardrails. The operational freedom provided to the business reduces tension and friction, elevates the security posture of the solution and promotes faster time to market.
At the end of the day security can either adapt to the new landscape, tap into the business and promote security whilst supporting the business or attempt to enforce antique controls, increase friction and become less relevant or even obsolete.